Cryptocurrency holders are facing a new subtle adversary – crypto dusting attacks.
If you have ever checked your digital wallet, you may notice a new coin appear — what is it? Has someone sent funds to you by mistake? Have you received an airdrop unexpectedly? Has your net worth just increased?
Don’t be fooled, it’s a phishing attempt designed to get access to your funds.
A crypto dusting attack is a method used by malicious actors to compromise the privacy of cryptocurrency holders.
Here’s how it works: attackers send minuscule amounts of cryptocurrency, or “dust”, to multiple wallets.
This “dust” is typically so small that it goes unnoticed by the recipient — but don’t be fooled by its size; this seemingly harmless amount can have significant implications.
To provide context, in the realm of Bitcoin, a satoshi (1 sat = 0.00000001 BTC) is considered “dust”.
If you find your wallet credited with such tiny amounts, you might be under an attack.
How Crypto Dusting Attacks Work
While dusting attacks don’t steal funds directly, they have a more insidious goal: compromising privacy.
By sending dust to various addresses and tracking its movement, malicious actors can link multiple addresses to a single wallet.
The process potentially unmasks the identity of the wallet holder, making them vulnerable to extortion, blackmail, or targeted phishing attacks.
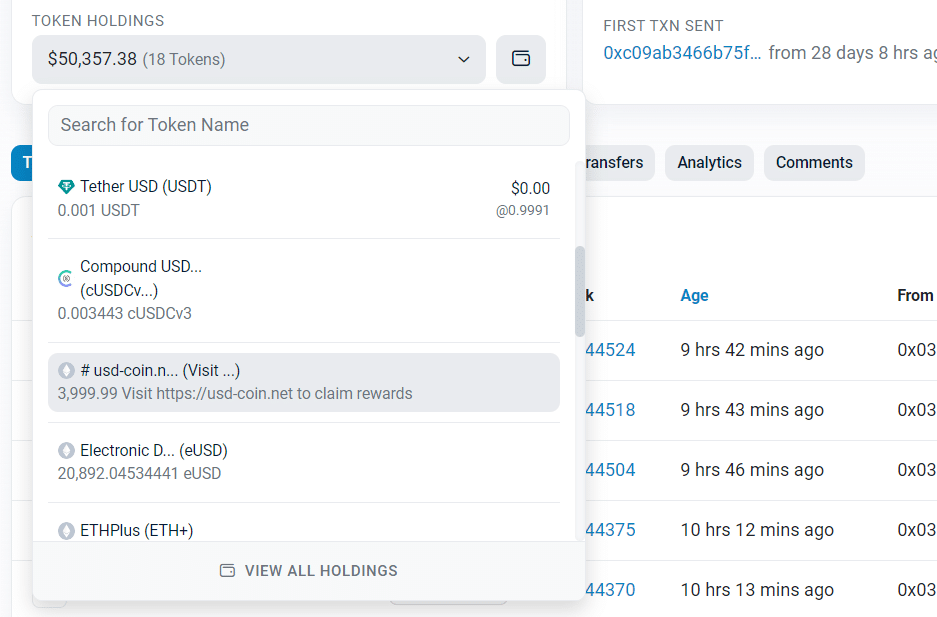
Alternatively, your “thousands of new tokens” — which are going to have a total worth of a fraction of a cent — may encourage you to visit a website “to claim your rewards”, or “bridge your tokens to a protocol”, or “connect your wallet and enter the ecosystem”.
All of this has one goal: to drain your wallet of real funds.
The only time something may be genuine “dust” is tiny fractions of tokens left after trading or exchanging. Ignore it, it is just a tiny remainder left after a transaction, again usually worth less than pennies.
Dusting in Action: A Very Real Threat
Recent times have seen notable dusting attacks.
The Samourai Wallet, for instance, had to warn its users about potential dusting, though they had countermeasures in place.
Another notable case occurred in 2020 when Binance’s Chain suffered a dusting attack – in this instance, attackers, besides sending minimal BNB tokens, also left a malicious link in each transaction memo.
Protecting Yourself From Dusting Attacks
Remember the cult classic WarGames, where the only way to win was not to play?
Similarly, the best defense against dusting attacks is not interacting with dust.
Spending it can link it to other wallets you own, revealing more about you.
However, the ideal solution isn’t always feasible – for those not keen on leaving the dust untouched, hiding or converting it is a safer option.
Major exchanges like Binance and Gemini or wallets like MetaMask allow users to hide tiny amounts. They can also offer to convert this dust, although this won’t have much effect on scam tokens of zero value.
For those wanting to go a step further, using a hierarchical-deterministic (HD) wallet provides an extra layer of protection.
An HD wallet creates a new public key for every transaction, ensuring attackers can’t trace any dust back to you.
The Bottom Line
Dusting attacks are a stark reminder of the constant evolution of cyber crime.
As blockchain technology and cryptocurrencies grow, so do the methods employed by those wishing to exploit them.
If attacks don’t lead to users following links to scam websites, the other threat is a compromise of a user’s privacy, which can lead to more significant outcomes down the line.
With companies becoming KYC compliant due to regulatory demands, dusting attacks might reveal even more personal data.
The key takeaway? Always keep an eye on your digital wallet, and be cautious of small, unexplained deposits – in the digital world, it’s always better to be safe than sorry.